Client Side is Still Bad
Category: Cryptography
Points: 150
Problem
I forgot my password again, but this time there doesn’t seem to be a reset, can you help me? http://2018shell.picoctf.com:8249 (link)
Hint
- Client Side really is a bad way to do it.
Solution
In this problem, we are just given a site and on opening that site we have a text box where we need to enter the credentials to find the flag. We can again use the inspect tool in most of the browsers to find out the flag as we did in Inspect Me problem.
Here are the steps which I followed to find the exact flag.
- Open the link in a new tab and you will reach the following page.

- Here we are asked of the credentials but we do not know but there is a hint provided that client-side is the bad way to do it hence let’s inspect the page using Ctrl+Shilt+I shortcut. So now our webpage looks like this.
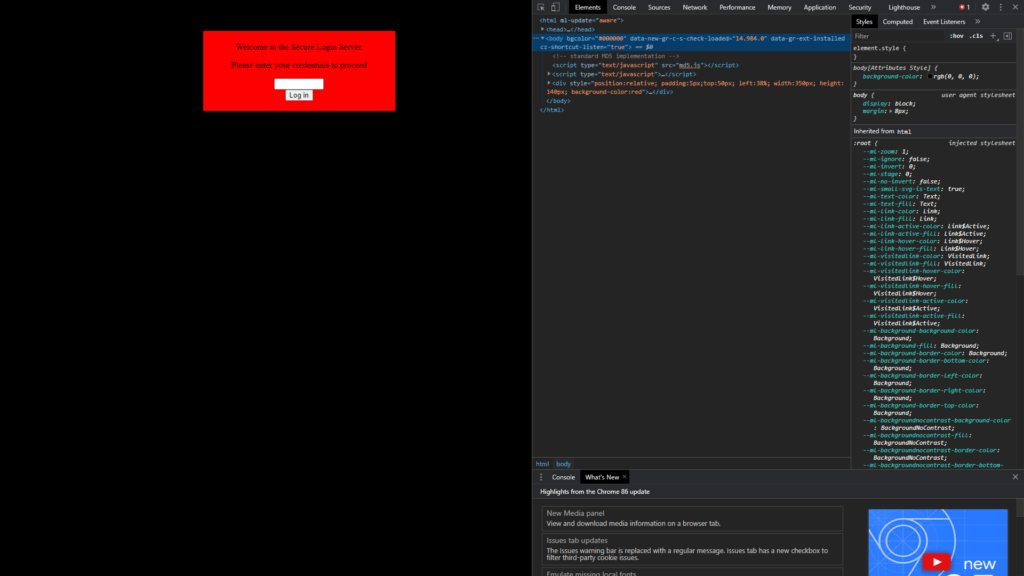
- Now we need to go to the sources tab in the Inspection window and locate the HTML file. HTML or HyperText Markup Language provides the skeleton to the website. You will see the following document.

- Now as we can clearly see the validation required using which the alert is created that “You got the flag”.

- The validation string starts with picoCTF hence we know that we have found the exact flag that we require. Upon entering the same in the textbox we get the alert that We got the flag and hence the solution to our problem.

Enter the same flag in the picoCTF website in the text provided for the solution and we have won 150 points.
Solution Flag
picoCTF{client_is_bad_9117e9}
For more capture the flag challenges visit CTF.
If you want to see Leetcode explained solutions visit Leetcode Solutions.
Check out my socials below in the footer. Feel free to ask any doubts in comment section or contact me via Contact page I will surely respond.
Happy Learning

